.png)
Software Engineering Intelligence
-
Intelligence Engine
On-demand exhaustive AI-analysis
-
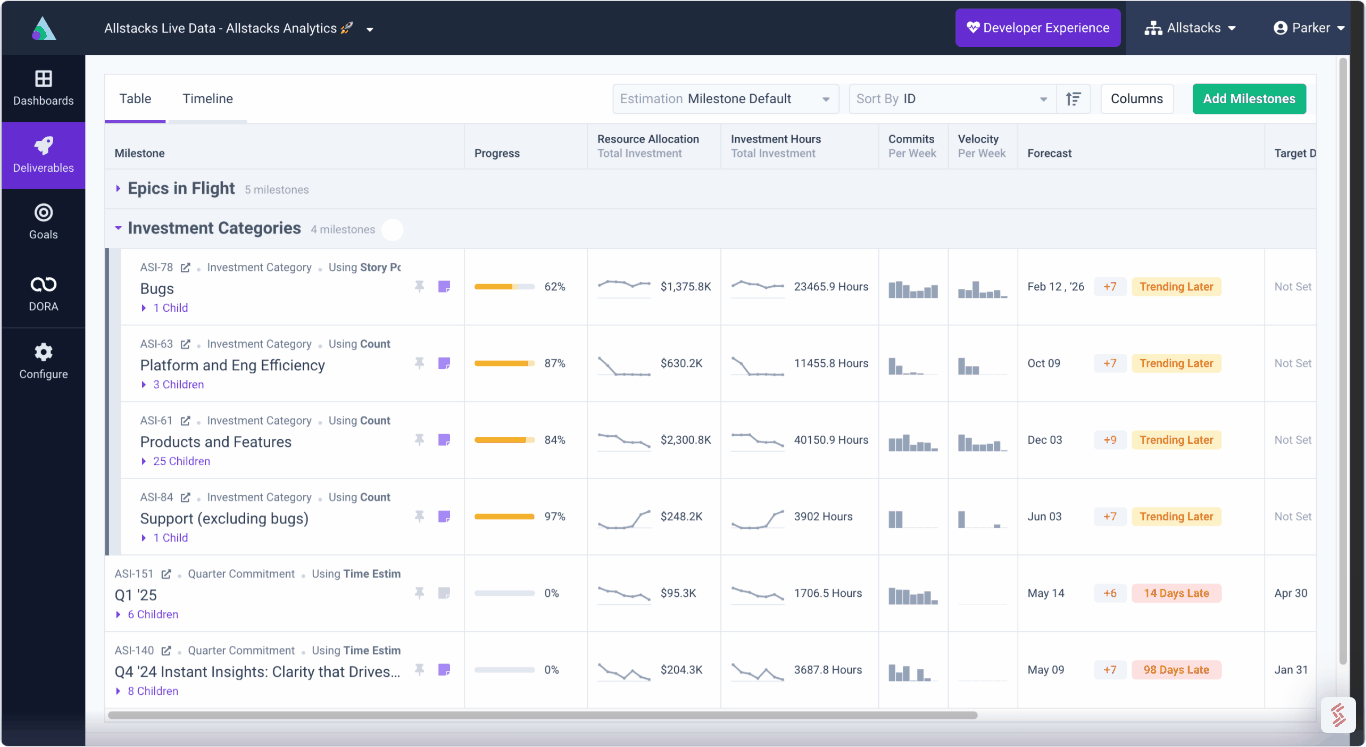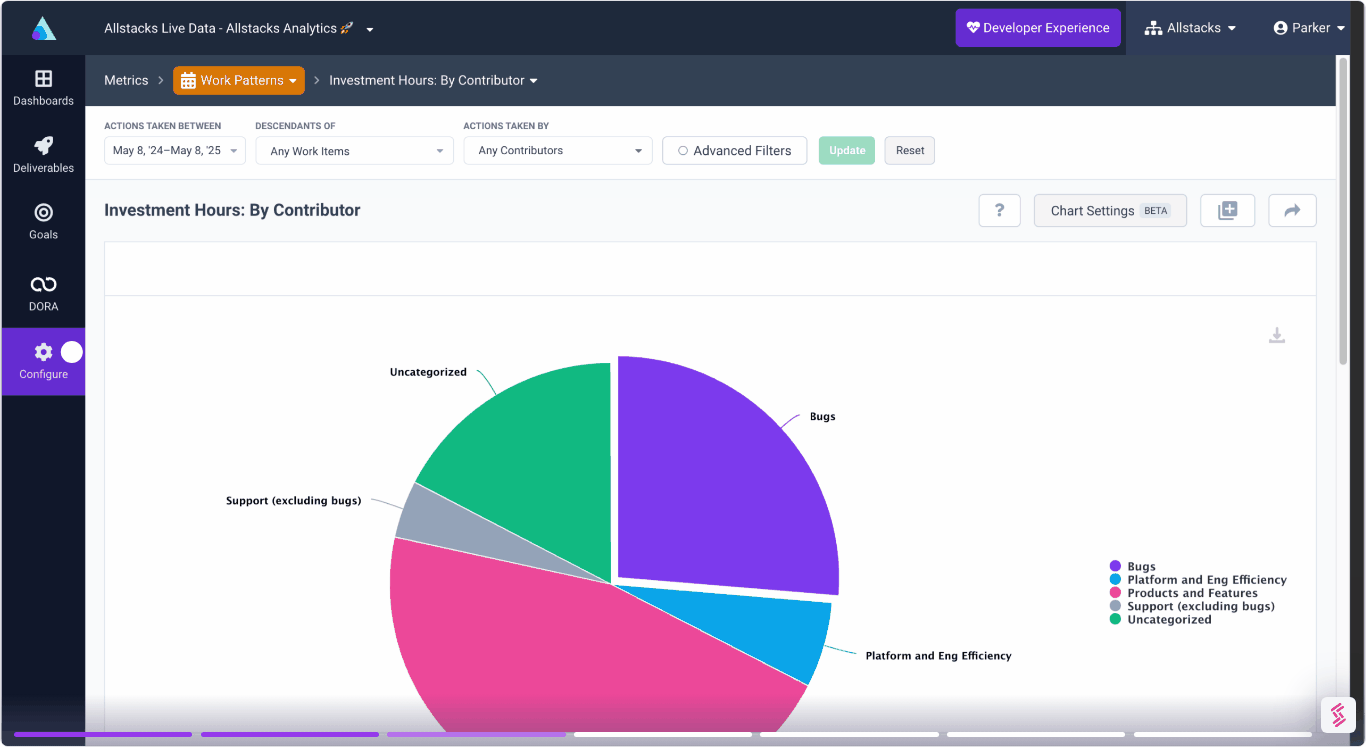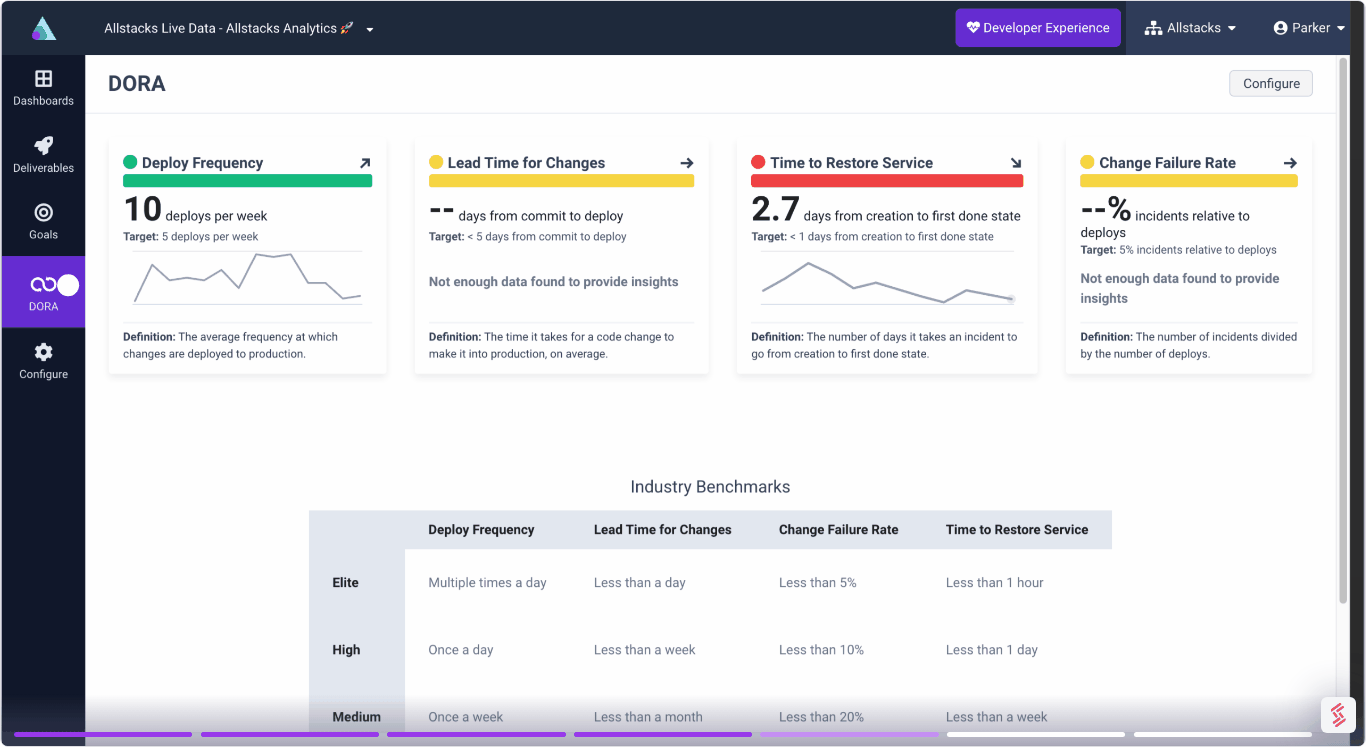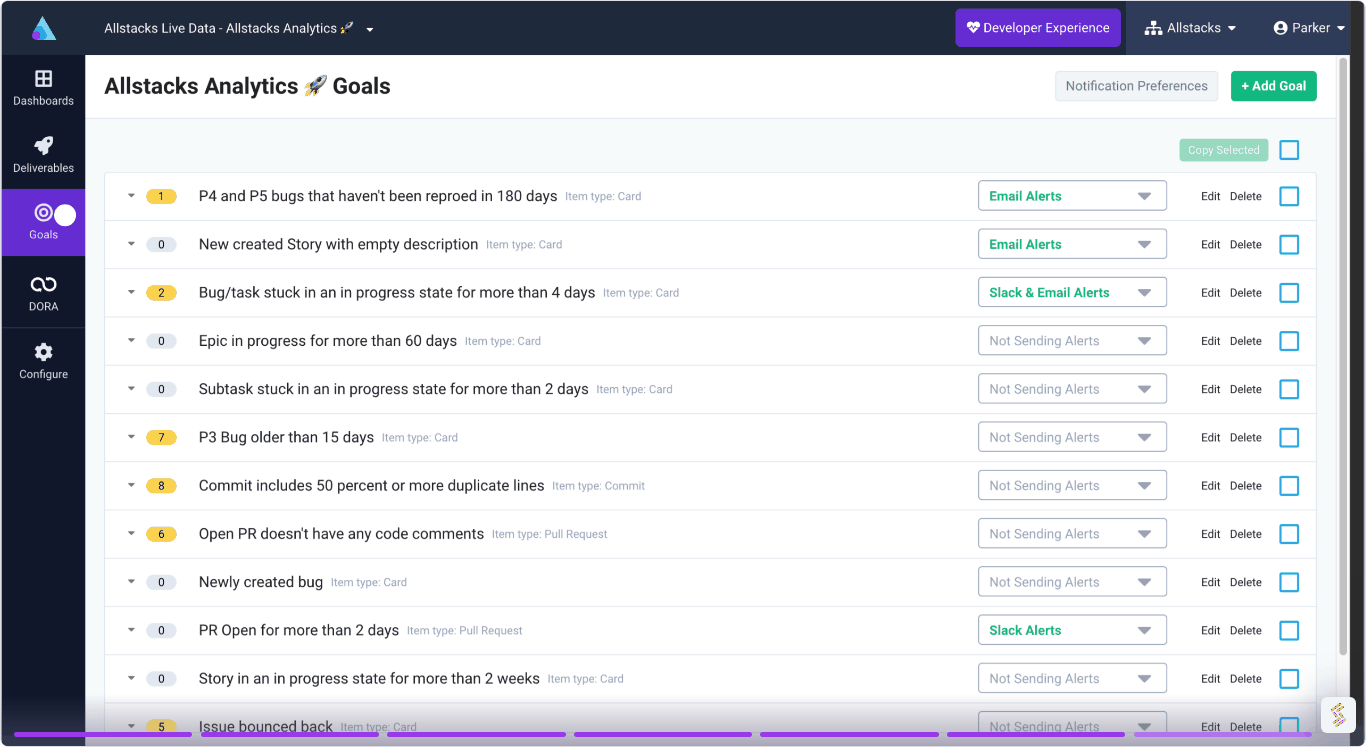
Engineering Investment
Complete visibility into time & dollars spent
-
360º Insights
Create meaningful reports and dashboards
-
Project Forecasting
Track and forecast all deliverables
DevEx
-
Developer Surveys
Create and share developer surveys
Software Capitalization
-
R&D Capitalization Reporting
Align and track development costs
Data Security
What data do we store?
As a SOC2 Type II certified organization, Allstacks makes every effort to bring you insights about your organization without storing any sensitive data. To that end, we only store metadata about your organization and your organization’s tools. We do not store full copies of source code, documentation, or private communication. Where our platform does inspect this data for analysis, it is transferred to the server, processed, and then immediately purged. We do not access or store private communication.
From each of your tools, we do store the following data for the purpose of data presentation:
- Usernames and/or email addresses,
- Repository Metadata (including: Project identifying information and statistics, pull request identifying information and statistics, commit identifying information and statistics, and issue identifying information and statistics),
- Project Management Metadata (including project identifying information and statistics, issue identifying information and statistics, and user access statistics).
- Unstructured communication on public forums and channels (Messages and comments)
Some Personally Identifiable information:
- Web cookies
- First or last names
- Email address
- Login name, screen name, nickname, or handle
What do we not store?
- Full Source Code or Full source code comments
- Budget or financial information
- Documentation or documentation contents
- Customer information (Unless added as a part of information we store above)
- Personal information of customers, clients, or external parties. (Unless added as a part of the information we store above)
- Private communication
Most personally identifying information, including:
-
- Home address
- National identification number
- Passport number
- IP address
- Vehicle registration plate number
- Driver’s license number
- Face, fingerprints, or handwriting
- Credit card numbers
- Digital identity
- Date of birth
- Birthplace
- Genetic information
- Telephone number
- Country, state, postcode or city of residence
- Age, especially if non-specific
- Gender or race
- Name of the school they attend or workplace
- Grades, salary, or job position
- Criminal record
All stored data is encrypted at rest in our cloud offering. Data handling for custom integrations and on premise installations is dependent on the provided hardware, infrastructure, and provider policies.
Access Credentials
Some software integrations only provide a “basic” authentication structure, which requires storing a username and password for access. In these cases, we store pertinent credentials in a secured database, salted and encrypted with a key stored externally to the database.
Access tokens, API tokens, OAuth and OAuth2.0 credentials, and other connection credentials are stored in a secured database, salted and encrypted with a key stored externally to the database.
Access credentials are persisted unless the user removes the connection to the service. This allows Allstacks to consistently update and refresh our data to provide you with the most accurate and timely view of your data.
How we process metadata
Allstacks processes data from a very large number of sources and takes your data privacy and sensitivity very seriously. After explicitly granting access to each tool, Allstacks downloads specific data sets for processing. Each data set undergoes a two-step process where (1) each download is scanned, and relevant metadata is stored in a persistent database. (2) This metadata is then processed to identify key metrics and insights, which are stored and presented on the platform.
Where is your physical infrastructure?
Allstacks stores all data with Amazon Web Services, and as such, benefits from the secured, distributed, fault tolerant environment provided by Amazon. Detailed information on Amazon’s security practices can be found here: https://aws.amazon.com/security/
Amazon continually manages risk and undergoes recurring assessments to ensure compliance with industry standards. Amazon’s data center operations have been accredited under:
- ISO 27001
- SOC 1 and SOC 2/SSAE 16/ISAE 3402 (Previously SAS 70 Type II) PCI Level 1
- FISMA Moderate
- Sarbanes-Oxley (SOX)
What security policies and procedures do Allstacks staff follow?
Allstacks restricts access to production servers and databases to a few, select, staff members. Security breaches are held as the highest level of infraction, and offenders are immediately terminated.
Allstacks supports a number of security policies that help restrict access to customers’ data:
- Data processing servers have routine access audits.
- Production datastores have routine access audits
- Credentials for Production datastores are only provided to a limited number of staff, and rotated with new staff members.
- Access is restricted to production and live data test servers to automated tools in order to minimize access levels needed by staff.
- Minimum password strength policies are in place.
Data Protection Statement Access
This document will be updated as features and security improvements are integrated into the system. An updated copy can always be obtained by contacting Allstacks at support@allstacks.com, and requesting an up-to-date copy of the data protection statement.
Resolution Avenues
All data requests can be made through the official communication channel at support@allstacks.com.
Any data can be removed upon request. This includes removal of the full set of data collected for an organization, a service, or an individual. This request should be made to the above address.
Data Retention
Customer data is not stored for longer that it is needed. We require data about employees and users to deliver accurate data visualizations, and remove this data either upon request, or after an audit period [30 days max] after the account is terminated.
Data is also removed if deemed out of date, or no longer valid. This can happen from removal of connected services, termination of accounts, or other events originating from connected service providers.